Hot Press News
- TiDB by PingCAP Leads Data Management Revolution at Great International Developer Summit 2024
- University of Birmingham Dubai invites applications for MSc Computer Science
- MindCypress Unveils Enhanced Advanced Digital Marketing Course with AI and ChatGPT Integration
- Launch of the book- A Monk with a Merc by Dr Gauravv Mittal Adit Mittal
- Elios 3 Drone Payload for UTM Introduced by Flyability and Cygnus
- Exterior Plas Marks 36 Years as Industry Leader in Windows, Doors and Glazing
- CD Bioparticles Announces Versatile Basic Agarose Particles for Efficient Biomolecule Separation
- Radisson Hotel Group strengthens its footprint in Delhi with the signing of Svelte Delhi
- Zee Business guides Investors to Navigate the Market with Confidence this Election Season
- Sandeep Marwah Inaugurates Scouts & Guides Marching Band at AAFT
- Scootaround Offered Event Rentals at NAB Show 2024
- Matrix Selected for the Outstanding MSME Excellence Award 2024
- Renowned Actress Radha Bhatt Conducts Acting Workshop at AAFT
- SIGMA launches Interchangeable Lenses for Canon RF Mount System
- Vedanta Aluminium organises 'AutoEdge' conclave, shares aluminium range for auto industry
 Mail to a Friend Mail to a Friend |
|
     |
7 Factors You Should Consider When Choosing a Joomla firewall for Your Website
2024-04-04 02:56:17
Technology
812
There is no doubt that the covid pandemic has driven all the businesses online. It has effectively increased the number of existing CMS users, Joomla being one of them. Joomla has always been popular because of its ease of use, and easy to target because of its poor security structure. The poor security structure of the Joomla website demands an additional layer of security that you can get by deploying an ideal firewall. You can go through a number of guides to improve the security of the Joomla store but nothing works as effectively as a Joomla firewall. In this article, we have compiled a list of factors you should consider before selecting a firewall to help you choose better.
Factors to consider while choosing a Joomla firewall
1. Deployment Options
There are mainly two architectural configurations associated with a firewall: in-line and tap/span. In inline architecture, the firewall is placed directly in between the requester?s traffic path and the server. The advantage of an inline architecture is that you can block a live attack on your website. But on the other side, the live interference will also block legitimate traffic to your website and will slow it down.
The second option tap/span is an example of passive architecture as the firewall is not placed in the same path as in an in-line architecture. The main advantage of a tap/span architecture is that it will not interfere with the traffic of your website. Our suggestion for you is to select a firewall with a hybrid architecture, i.e; a firewall that can protect your website?s server at both inline-level as well as cloud-level.
2. Detection Techniques
After taking deployment options into consideration, it is important to ask: What are the detection techniques used by the firewall? Nowadays, most Joomla firewalls use a combination of different detection techniques for more accurate detection coverage. These techniques include normalization, signatures, rules, APIs for custom detection. Some firewalls are also capable of behavior analysis, they can learn the normal traffic pattern of your website and detect the vulnerabilities specific to your website.
Do not forget to ask your vendor about the techniques in use and also ask them to give proof of positive test results to get a better idea of the effectiveness of the firewall.
3. Protection
There are various protection techniques in which a Joomla firewall ( https://www.getastra.com/blog/cms/joomla-security/joomla-firewall-joomla-antivirus/ ) can block traffic. Before choosing the firewall, look for the options that meet your website?s security needs. These techniques include:
● Connection-intermediation: In this protection technique, the firewall intercepts the traffic and terminates all the network protocol connections.
● Connection Interruption: In this protection technique, the firewall intercepts the traffic, but does not terminate the connections.
● Connection reset: The firewall intercepts the traffic and resets all the relevant TCP connections.
● The firewall will alert other devices to block suspicious traffic.
If you are looking for a firewall that includes traffic blocking, be sure to be aware of different approaches to traffic blocking, such that; at what levels it can block traffic?, Can it block specific users or IP addresses? etc.
Some additional desirable features of an ideal Joomla firewall are:
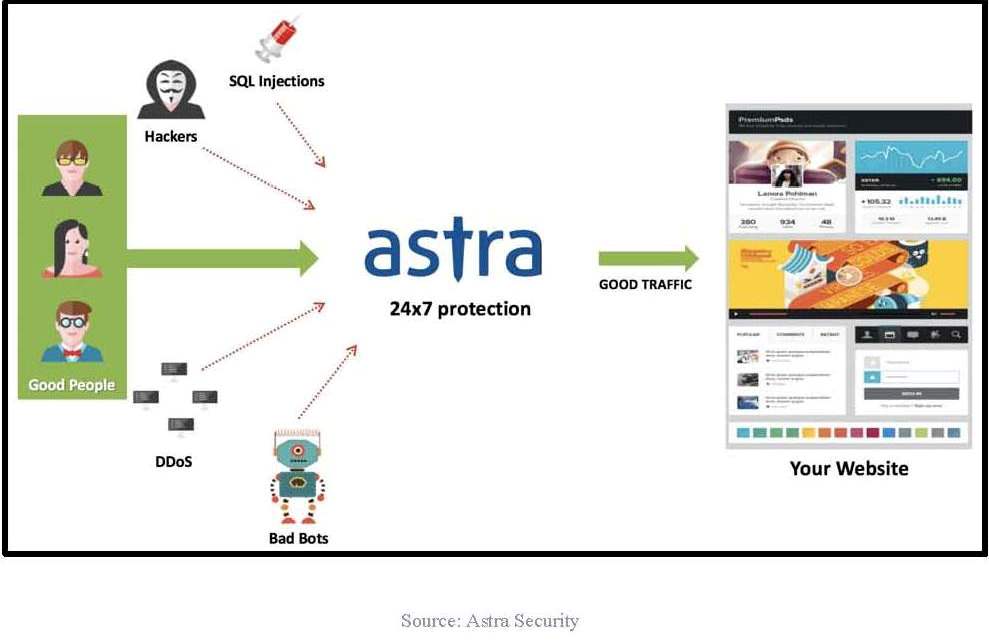
● Protection against known attacks such as XSS, SQLi, CSRF, DDoS, etc;
● Bad bot blocking,
● Protection from zero-day threats,
● Attacker profiling,
● Suspicious Login Alerts,
● Threat analytics.
4. Compatibility and scope of Customization
Compatibility of a firewall with your other network equipment is as important as it is to look for the security features in a firewall. Your firewall should never interfere with the behavior of your website. Therefore, before choosing a firewall check whether it is compatible with your website or not.
Also make sure that the firewall is customizable in terms of aspects, policies, and rules as they might change in the future. Because trust me, you would not want to change the firewall every time a new policy is added!
5. Logging and Reporting
Another important factor to look for in a Joomla firewall is the way a firewall logs data. The logging and reporting interface of a firewall are decisive factors in choosing a firewall. Ask your vendor how detailed logs are? Does the firewall maintain separate logs for legitimate traffic and suspicious traffic? The more detailed the log is, the easier it will be for you to take security measures and do changes to your website.
Apart from the logging interface, ask your vendor about the types of reports the firewall can supply and compare them with your security checklist. Also, see if the reports can be generated on-demand and scheduled.
6. Compliance
Although most of the firewalls are compliant with PCI-DSS, it is essential for a firewall to be compliant with the security standards followed by your website. Ask your supplier whether or not the firewall can be configured to detect sensitive data automatically.
7. Support
If your website requires 24?7 support, go for a firewall that has the security team available 24?7?365. The support team of a firewall can be a decisive factor while choosing a Joomla firewall. Because who wouldn?t want their website to be monitored 24?7? Also, ask your supplier about how often the updates are performed? Timed updates are important for the performance of a firewall.
To Conclude!
Hopefully, this article was able to shed light on all the key points to consider while choosing a Joomla firewall. But if you are still having difficulty in choosing a firewall, here is our suggestion: Astra Security. The excellent security team and ever-evolving AI of Astra are what you need to safeguard your website completely. Astra will not only protect your website from external known and unknown threats but will also monitor your website actively.










